Arjybeasts
A turn based RPG where you create pixel characters called Arjybeasts, whose RGB values determine their power in battle.
Systems Programmer
July 2023 - Ongoing
Responsibilities + Skills Used:
-
Adaptor / Mediator Programming Pattern
-
Frequent usage of Refactoring
-
Storing and Loading player character and data
-
Creating an obfuscation algorithm
-
Kanban methodology
-
Removed technical limitations to allow for Game Feel
Look out for the release on
Steam!
Arjybeast Creator
An Arjybeast is an image the player creates, and I was responsible for implementing the 'software' that could be used to draw them.
The design was based off of Microsoft Paint (the software was named 'Pant').
I made use of the Mediator design pattern to integrate many different painting functions easily, including:
-
Selecting colors
-
Drawing / Erasing / Fill Tool / Eye dropper
-
Editing the Hue / Saturation / Value of the image
-
Adding colours to your palette
-
Undo function
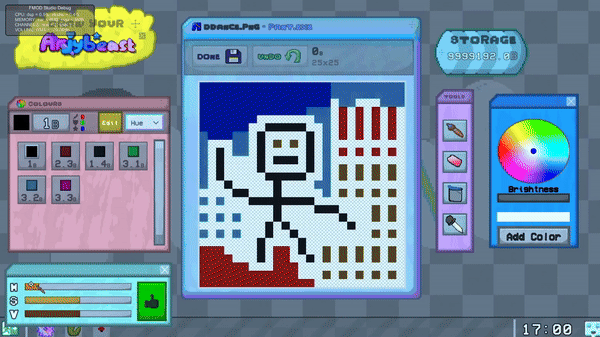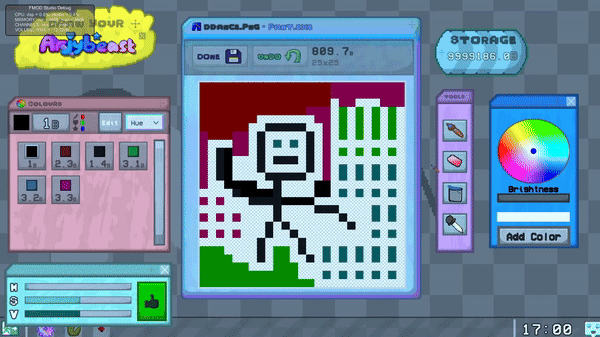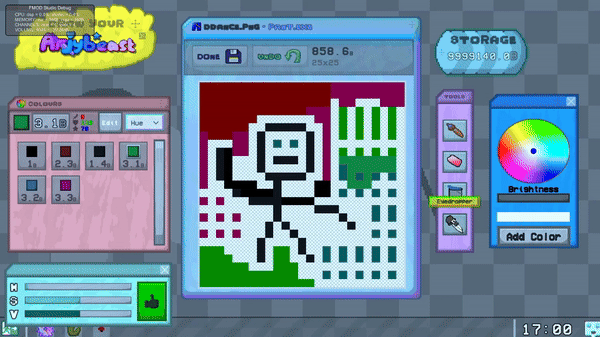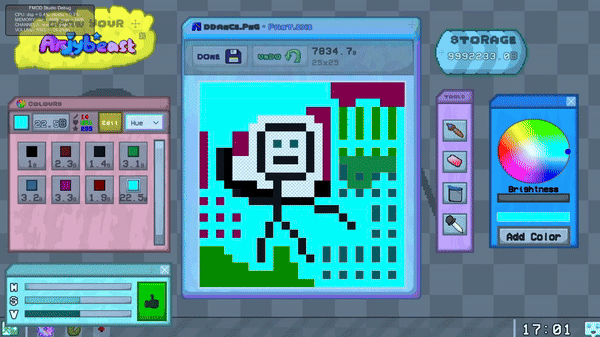
Each element in the editor communicates with a central Pant Manager 'brain', reqesting it to perform actions like coloring a pixel, adding a color, or setting the currently selected color.
The Pant Manager either approves or denies these actions based on the state of certain variables.
[diagram here]
Obfuscation Algorithm
We stored the 'Arjybeast' files in the project at the risk of the player easily editing the enemies in the game.
To mitigate this, I created an Obfuscation algorithm to encodes an arjybeast data file into an unreadable string.
The goal was to create a string that hides a hidden message to keep in line with the lighthearted tone of the game, rather than something cryptographically secure.

→
"Jimmy the Lock"
25x25
Move A, Move B, Move C
ARJYBEAST YEABB JRAY JSJTE JBJEJ JYBYA JTERS BJEE EBAT EATR RERJS JBSAE YSBYT JJAYA YBERY YRYBA YSBBT JABY JJSE JBTY RBJAT RYJTA RABES RJSJA RRTYT RRYRR EAAT EYJY ESYT SJAR SESE TREY RJRTS RAREA RAEEE RRJAE RRSYR JSBAR...
.png)
→
"Suitcase"
18x18
Move D, Move E
!suitcase!isceu!cessc!ccusc!caiat!ciitt!eiess!aecs!cssis!acuec!usctu!eutuu!esaua!uitac!icuei!ccaeu!aac...
The obfuscation process involves these steps:
Provide data to encrypt, and a key whose characters will be used in the final string, and a separator character.
Convert the data into an array of bytes based on UTF32, and XOR each byte with the index in their list.
UTF32 was chosen to handle all possible characters.
XOR was chosen as it's an easily reversible operation and adds an extra layer of obfuscation.
Use Szudzik Pairing to combine each pair of numbers into one number.
This pairing algorithm was used to prevent manual decryption. Pairing is a simple equation, but unpairing requires a much longer process.
Convert the final numbers to text, using the unique characters from the key as 'digits', and the separator character to separate each 'number'
The key is extracted by finding the text between the first two occurences of the separator character. The characters in the key don't matter, as long as they don't include the separator character.
[diagram here of steps]
FMOD Adaptor Pattern
[...]




